I once assumed strong passwords kept accounts secure.
But security reviews showed otherwise—most breached accounts had valid credentials that were stolen or phished.
What stood out even more was that 2FA wasn’t failing because it was missing, but because it wasn’t tested well.
Delayed OTPs, broken push prompts on older devices, non-expiring backup codes, and drifting TOTP tokens all opened quiet gaps attackers could use. The takeaway was unmistakable: 2FA protects only when every path and edge case is tested carefully.
Overview
Two-Factor Authentication (2FA) is a security method that prevents unauthorized access by requiring users to verify their identity with two independent factors—typically a password plus a second step such as an OTP, authenticator app code, or biometric.
Types of 2FA Mechanisms to Test
- SMS OTP
- Email OTP
- TOTP (Authenticator apps like Google Authenticator)
- Push-based 2FA (e.g., device prompts)
- Hardware tokens
- Backup codes
- Biometric fallback flows
In this guide, I’ll walk through how to properly test Two-Factor Authentication, along with real use cases that highlight issues teams often catch only after a breach or user complaint.
What is Two Factor Authentication (2FA)?
Two-Factor Authentication (2FA) is a security method that requires two separate forms of verification before granting access. In practice, this means a user enters a password first and then confirms their identity with a second step—like an OTP, an authenticator app code, or a biometric scan—to ensure the account stays protected even if the password is stolen.
Unlike simple authentication, which relies only on a username and password,Two-Factor Authentication adds an extra layer that attackers cannot bypass without the second factor. This makes unauthorized access far harder, reducing the risk of account compromise.
Types of Authentication Factors
Authentication factors fall into three main categories, each verifying identity in a different way. Strong security often comes from combining factors from more than one category.
- Knowledge factor (Something you know): Includes passwords, PINs, and security questions that rely on user knowledge.
- Possession factor (Something you have): Covers physical or digital items such as SMS/email OTPs, authenticator app codes, hardware tokens, or smart cards.
- Inherence factor (Something you are): Uses biometric traits like fingerprints, face recognition, voice ID, or iris scans for verification.
How does Two-Factor Authentication Work?
Here’s How Two-Factor Authentication (2FA) Works:
- User enters username and password: The system checks the primary credentials just like standard login.
- System triggers a second verification step: This may be an OTP, authenticator app code, biometric prompt, push notification, or hardware token.
- User provides the second factor: The user enters the OTP, approves the push notification, scans their fingerprint, or uses the required device.
- System verifies both factors: Access is granted only if both the password and the second factor match.
- Login is completed securely: Even if a password is compromised, attackers cannot log in without the second factor.
BrowserStack App Live is a cloud-based testing tool, that lets you verify each 2FA step on real iOS and Android devices, ensuring OTP delivery, authenticator apps, and push prompts behave as expected. It helps you uncover device-specific issues early so every authentication flow works reliably for users.
Benefits of Two-Factor Authentication?
Two-Factor Authentication strengthens account security by adding a second layer of verification beyond passwords. This reduces the risk of unauthorized access and improves overall user protection.
- Prevents credential-based attacks: Even if a password is stolen through phishing, brute force, or data breaches, attackers cannot access the account without the second factor.
- Protects sensitive user data: Financial, personal, and organizational information remains secure behind multiple verification layers.
- Reduces fraud and identity theft: Extra authentication steps block impersonation attempts and unauthorized transactions.
- Secures high-risk user actions: Activities like password resets, financial transfers, or profile changes are protected with an additional check.
- Improves trust and compliance: Many security standards and regulations (e.g., PSD2, PCI DSS) strongly encourage or require 2FA, helping organizations meet compliance goals.
Types of Two-Factor Authentication Mechanisms to test
Two-Factor Authentication can be implemented in several ways, and each mechanism introduces unique behaviors, failure points, and testing requirements. Validating these mechanisms ensures authentication works reliably across devices, networks, and user conditions.
- SMS OTP (One-Time Password): A code sent via text message. Needs testing for delivery delays, carrier variations, incorrect codes, expiration time, and retry limits.
- Email OTP: A verification code delivered to the user’s inbox. Testing involves email latency, spam filtering, link formatting, code validity, and cross-device access.
- TOTP (Time-Based One-Time Password): Codes generated by apps like Google Authenticator or Authy. Requires testing for time drift, setup process, QR code scanning, token sync, and expiry behavior.
- Push-Based Two-Factor Authentication: The user receives a push notification on their device to approve or deny login. Testing must cover device registration, notification reliability, OS-level restrictions, and offline scenarios.
- Hardware Tokens: Physical devices like RSA tokens or USB security keys (e.g., YubiKey). Testing involves device detection, token sync, insertion failures, and fallback flows.
- Biometric Verification: Authentication via fingerprint, face recognition, or voice ID. Tests should include biometric enrollment, false reject scenarios, sensor errors, and device-specific differences.
- Backup Codes: One-time recovery codes used when other factors are unavailable. Testing ensures codes are unique, usable once, securely stored, and invalidated after use.
Use Cases of Two-Factor Authentication
2FA is applied across critical user journeys to protect accounts, transactions, and access points from unauthorized activity. Each use case addresses a specific security risk and ensures the user’s identity is verified beyond a simple password.
- User Account Creation: Verifies that a new account is being created by the legitimate user, preventing bots or attackers from using stolen email addresses or phone numbers.
- Account Recovery: Adds a second check during “Forgot Password” or profile recovery flows to prevent unauthorized users from taking over accounts with compromised credentials.
- Financial Transactions: Secures high-value actions such as money transfers, payments, or changes to financial information by requiring OTPs or approval prompts.
- Network and VPN Access: Ensures only authorized individuals can access internal networks or enterprise systems, often using hardware tokens or authenticator apps.
- Login from Unknown Devices or Locations: Triggers an additional verification step when login attempts occur from unfamiliar browsers, IPs, or geographies to block suspicious activity.
To understand how 2FA works for user account creation, here’s an example of login into the LinkedIn account.
Step 1 On the sign-in page, once the user has entered their user id and password details.
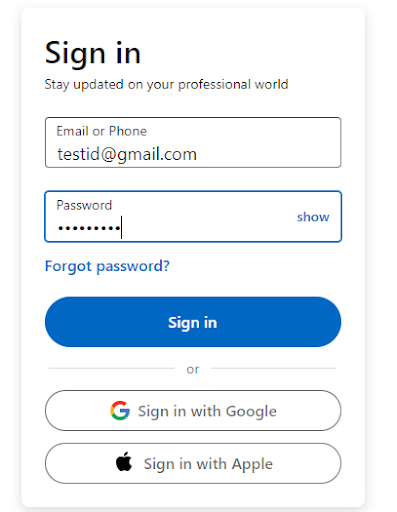
Step 2 A security code will be asked if 2FA is enabled for the user.
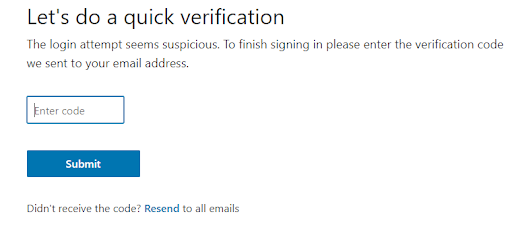
If the Two-Factor Authentication is not enabled, here’s how you can enable it.
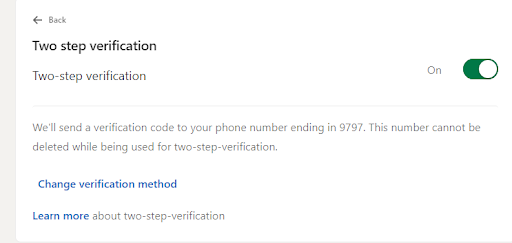
Challenges in Testing Two-Factor Authentication
Here are some of the notable challenges in testing 2FA:
- Dependency on external services: 2FA relies on SMS gateways, email providers, and push services, which can introduce delays or failures that affect test consistency.
- Variability across devices and networks: OTP delivery and behavior differ by device model, OS version, carrier, and network strength, making issues hard to reproduce.
- Handling time-based tokens: TOTP mechanisms depend on precise time sync, and even slight clock drift between server and device can cause token failures.
- Limited automation capabilities: Steps like reading SMS codes or approving push notifications are difficult to automate without mocks or specialized setups.
- Testing negative and edge cases: Validating expired OTPs, repeated failures, slow networks, or lost-device scenarios requires controlled test environments.
- Secure handling of test data: Managing phone numbers, email inboxes, and credentials must be done securely to avoid exposing sensitive test information.
Security Best Practices for 2FA Implementation
Applying strong security measures ensures that 2FA not only enhances protection but also avoids creating new vulnerabilities within authentication flows.
- Use short-lived OTPs: Limit OTP validity to a brief window (typically 30–60 seconds) to reduce the risk of intercepted or reused codes.
- Enforce rate limiting: Prevent attackers from brute-forcing OTPs by restricting the number of attempts allowed within a given time.
- Invalidate codes after one use: Ensure OTPs and backup codes cannot be reused, even if intercepted or guessed.
- Protect backup and recovery methods: Secure fallback options like email links or recovery codes, which often become the weakest link if not handled properly.
- Secure communication channels: Deliver OTPs and notifications through encrypted channels and avoid exposing sensitive data in logs.
- Implement device binding: Link authenticator apps or push-based 2FA to a specific device to prevent unauthorized enrollment or cloning.
- Monitor for suspicious activity: Track unusual login patterns, repeated OTP failures, or device changes to detect potential abuse.
- Use secure time sources for TOTP: Ensure accurate server-side time synchronization to prevent token validation errors.
- Validate on real devices: Test 2FA flows across real iOS and Android devices to confirm consistent behavior under real network conditions, device states, and OS-level variations.
BrowserStack App Live lets teams validate 2FA security measures on real iOS and Android devices, ensuring OTPs, authenticator apps, and fallback methods behave correctly under real-world conditions. It helps uncover device-specific or network-related issues that may weaken authentication flows.
Tools & Platforms for Testing Two-Factor Authentication
Testing Two-Factor Authentication requires solutions that can handle OTP delivery, multi-device verification, network variations, and automation constraints. The following categories help teams validate both functional and security aspects of 2FA.
- Real device cloud platforms: Services like BrowserStack App Live allow testing Two-Factor Authentication flows on actual iOS and Android devices, ensuring OTP delivery, push notifications, and biometric prompts work reliably across device and OS variations.
- Email testing tools: Tools that provide test inboxes or email capture allow teams to verify OTP emails, link formatting, latency, and expiration behavior without relying on personal accounts.
- SMS testing gateways: Virtual phone numbers or SMS capture APIs help teams validate SMS OTP delivery, delays, retry limits, and formatting under controlled conditions.
- Authenticator app test environments: Tools that support TOTP setup, QR code scanning, and time sync testing help validate implementations using Google Authenticator or similar apps.
- Automation frameworks with mocking capabilities: Frameworks that allow bypassing or mocking 2FA steps in CI environments help maintain automated test coverage without exposing real credentials or OTPs.
Why choose Browserstack to test Two-Factor Authentication?
BrowserStack App Live provides the real-device coverage, reliability, and debugging depth required to test 2FA flows accurately—something emulators and local setups often fail to deliver.
- Test on real iOS and Android devices: Validate SMS OTPs, email OTP access, authenticator app codes, and push notifications on actual devices, not simulated environments.
- Reproduce real-world conditions: Check 2FA behavior across different networks, OS versions, device models, and carrier variations that impact OTP delivery and timing.
- Verify biometric prompts accurately: Ensure Face ID, Touch ID, and other device-level authentication flows work consistently across the devices your users rely on.
- Instant access to thousands of device–OS combinations: Quickly identify device-specific 2FA failures—from token delays to notification issues—without maintaining an in-house device lab.
- Deep debugging tools: Use videos, logs, screenshots, and network insights to troubleshoot failures in OTP delivery, push notifications, or app state transitions.
- Secure testing environment: Protected sessions ensure safe handling of sensitive data, test credentials, and authentication flows during 2FA validation.
- Faster test cycles with on-demand devices: Test whenever needed without waiting for physical devices, helping teams validate critical authentication paths quickly before release.
Conclusion
When I test 2FA, the goal is to confirm that every authentication method works reliably across devices, networks, and edge cases—not just that an OTP arrives. Looking at failure paths, timing variations, and device-specific behavior reveals issues long before users ever encounter them.
Running these checks on real devices with BrowserStack makes the process clearer and more grounded. I can see exactly how OTPs, authenticator apps, and multi-device flows behave in real conditions, which highlights strengths and exposes gaps quickly. It turns 2FA testing into a focused, predictable process and helps ensure the final authentication experience is solid for every user.